Defense PolicyHuman Rights
Commissions Impossible: How Can Future Military Commissions Avoid the Failures of Guantanamo?
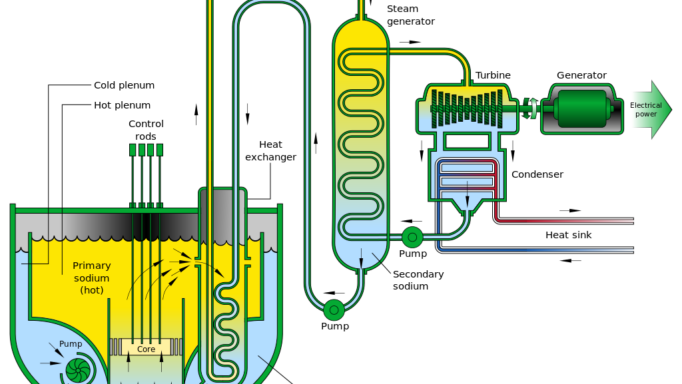
Emerging TechnologyNuclear Weapons
Advanced Reactors and Nuclear Terrorism: Rethinking the International Framework
Terrorism and CounterterrorismThe Constitution
An Army Turned Inward: Reforming the Insurrection Act to Guard Against Abuse
Foreign PolicyInternational Security
Managing the Terrorism Threat with Drones
Defense PolicyInternational Security
Drone Strike—Analyzing Public Perceptions of Legitimacy
Defense PolicyInternational Law
Over-the Horizon Drone Strikes in an Ongoing Global War: Afghanistan and Beyond
International LawInternational Security
Analyzing the Legality and Effectiveness of US Targeted Killing
International SecurityReligious Extremism
Analyzing the Impacts of Targeted Killing: Lessons for the United States
Human RightsInternational Law
ISIL as Salesmen? The Roles of Due Diligence and the Good Faith Purchaser in Illicit Artifact Trafficking
CybersecurityReligious Extremism
Social Media—A Tool for Terror?
Defense PolicyForeign Policy
By, With, And Through: Section 1202 and the Future of Unconventional Warfare
Terrorism and Counterterrorism
“Outside Experts”: Expertise and the Counterterrorism Industry in Social Media Content Moderation
Refugees and ImmigrationTerrorism and Counterterrorism
Turning US Vetting Capabilities and International Information-Sharing to Counter Foreign White Supremacist Terror Threats
Terrorism and Counterterrorism
Lessons for the Next Twenty Years: What We’ve Learned in the Two Decades Since 9/11
Terrorism and Counterterrorism
Rethinking U.S. Efforts on Counterterrorism: Toward a Sustainable Plan Two Decades After 9/11
Laws of WarTerrorism and Counterterrorism
“Until They Are Effectively Destroyed”: The U.S. Approach on the Temporal Scope of Armed Conflicts with Terrorist Organizations
Religious ExtremismTerrorism and Counterterrorism
Managing Terrorism
Human RightsInternational Law
Preventive Detention for National Security Purposes in Israel
Laws of WarTerrorism and Counterterrorism
The Covert Action Statute: The CIA’s Blank Check?