CyberespionageEmerging Technology
Deepfake 2024: Will Citizens United and Artificial Intelligence Together Destroy Representative Democracy?
CybersecurityDefense Policy
A New Framework for Cyber Operations: Reevaluating Traditional Military Activities and Intelligence Collection in the Digital Age
Foreign PolicyInternational Security
The San Francisco Conference and the Evitable UN Vetoes
Foreign PolicyIntelligence
Influence, War, and Ethics
International LawInternational Security
The Protection of Nationals Abroad and Non-Combatant Evacuation Operations in Times of Crisis
Foreign PolicyThe Constitution
Congressional and Supreme Court Restraints on Treaty Termination Carried Out at the President’s “Lowest Ebb” of Authority
Emerging TechnologyNuclear Weapons
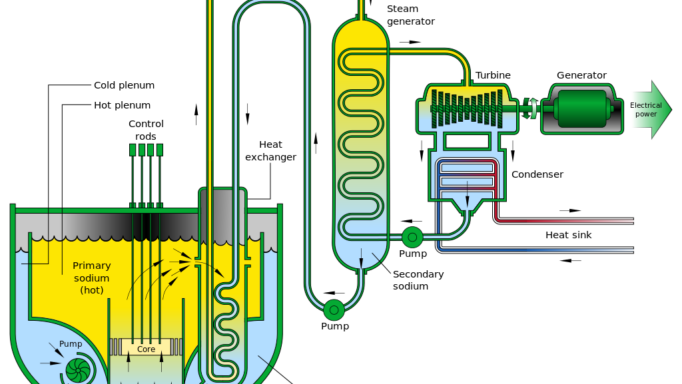
Advanced Reactors and Nuclear Terrorism: Rethinking the International Framework
Foreign PolicyThe Constitution
A Bellicose Founding Charter: The US and Providing for the “Common Defence”
Foreign PolicyInternational Law
China’s Anti-Monopoly Merger Control and National Security: Interactions with Foreign Investment Law and Beyond
International LawInternational Security
Lawfare and Sea Power: A Historical Perspective
Human RightsInternational Law
The Case for Attempted Perfidy: An “Attempt” to Enhance Deterrent Value
Terrorism and CounterterrorismThe Constitution
An Army Turned Inward: Reforming the Insurrection Act to Guard Against Abuse
Foreign PolicyInternational Security
Managing the Terrorism Threat with Drones
Defense PolicyForeign Policy
Endless War Challenges Analysis of Drone Strike Effectiveness
Defense PolicyInternational Security
Drone Strike—Analyzing Public Perceptions of Legitimacy
Defense PolicyInternational Law
Over-the Horizon Drone Strikes in an Ongoing Global War: Afghanistan and Beyond
International LawInternational Security
Analyzing the Legality and Effectiveness of US Targeted Killing
International SecurityReligious Extremism
Analyzing the Impacts of Targeted Killing: Lessons for the United States
Human RightsInternational Law
ISIL as Salesmen? The Roles of Due Diligence and the Good Faith Purchaser in Illicit Artifact Trafficking
Human RightsInternational Law
Migrants as a Weapons System
Defense PolicyMilitary Law
The First Calling Forth Clause: The Constitution’s Non-Emergency Power to Call Forth the Militia to Execute the Laws
CyberespionageIntelligence
Willfulness and the Harm of Unlawful Retention of National Security Information
CybersecurityEmerging Technology
A Multiverse of Metaverses
CybersecurityReligious Extremism
Social Media—A Tool for Terror?
Foreign PolicyInternational Security
FDI Like You’re FDR: CFIUS Review Under the Biden Administration’s Rooseveltian Conception of National Security
Defense PolicyForeign Policy
By, With, And Through: Section 1202 and the Future of Unconventional Warfare
Terrorism and Counterterrorism
“Outside Experts”: Expertise and the Counterterrorism Industry in Social Media Content Moderation
Laws of WarThe Constitution
The Selling of a Precedent: The Past as Constraint on Congressional War Powers?
Law and Security in Space
Olive Branches or Fig Leaves: A Cooperation Dilemma for Great Power Competition in Space